How to use tor browser correctly?
How to download tor browser?
If you want to learn more about Tor Browser, it means you already know the importance of online privacy and anonymity. Because Tor Browser is a great tool to help you stay safe online. But regarding its advantages and disadvantages, especially the relationship between it and VPN, many people still don’t understand.
This guide aims to answer the above questions and other questions. We will explain here how this powerful tool works and the factors you should consider when deciding whether it is right for you.
What is Tor Browser?
The Tor browser is similar to a normal web browser in many ways. The ease of use is similar to that of Google Chrome or Microsoft Edge. The difference is that the Tor browser connects you to the Internet through the Tor network.
Tor is free and open source software that can help you stay anonymous online. When you use the Tor browser to browse the Internet, your traffic will be randomly directed through the server network before reaching the final destination to protect your location and identity.
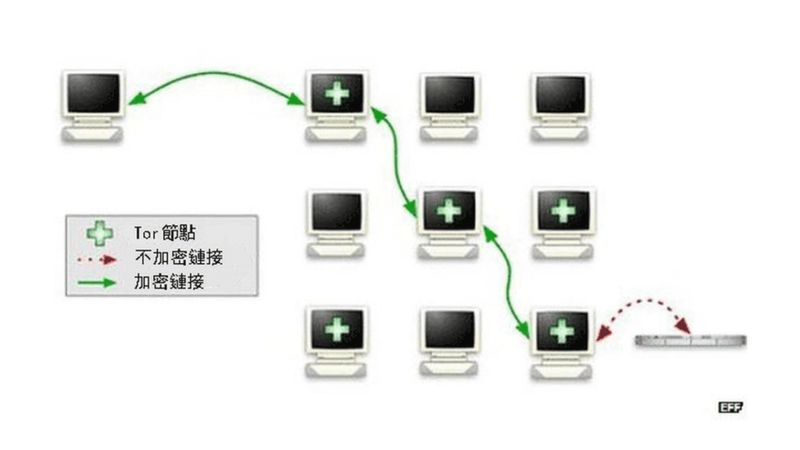
“Tor” is the abbreviation of “The Onion Router”, reflecting the way Tor protects its data by wrapping it in multiple encryption layers (like onions).
Is Tor Browser a VPN?
Tor browser and VPN are both tools used to protect online privacy. However, they are two different things. It uses completely different technologies and in different ways to protect your safety.
VPN protects all data through end-to-end encryption, and then directs it to a remote server through a secure channel, which will then connect you to the website you want to visit.
We will explain below how Tor Browser protects your privacy in different ways.
The important thing is that Tor browser is different from VPN, but you can use these two tools together to ensure your safety and privacy are not leaking.
How does the Tor browser work?
Although the background system of Tor Browser is very complicated, it is very easy to use. You only need to download and install the Tor browser, and you can connect to the Internet like any other browser.
Tor uses a unique system developed by the US Navy to protect government intelligence communications.
Your data will be bundled into the encrypted packet layer before entering the Tor network. Then it is routed through a series of servers (called nodes or relays) operated by volunteers.
Every time data passes through a relay, a layer of encryption is removed to show the location of the next relay. When the data reaches the final relay (known as the “exit node”), the last layer of encryption will be removed, and your data will be sent to its final destination.
Each relay only decrypts the data that helps to understand the location of the previous and next relay. Since each path is randomly generated and no relay record is kept, it is difficult for anyone to trace your footprint through Tor’s complex network.
Is Tor Browser safe?
The Tor browser can effectively hide your location and prevent your traffic from being tracked, making it difficult for anyone to trace your online activities through the Tor network.
However, the Tor browser is not without loopholes. This system has some disadvantages. Since every server in the Tor network is operated by volunteers, you never know who owns the relay for data transmission.
Usually, because each relay-except for the egress node-can only learn the location of the previous and next relay, this is not a problem.
The exit node will delete the last layer of encryption of the data. Your original location or IP address will not be seen, but if you visit an insecure HTTP website, the exit node may use this to monitor your activities.
In addition, Tor browser is as vulnerable to similar attacks as other browsers. If you want to remain anonymous, it is best to turn off browser plug-ins and scripts, because they may reveal information such as your IP address.
What are the disadvantages of Tor Browser?
The biggest disadvantage of using Tor browser is speed. Since your data must pass through multiple relays before reaching the final destination, your browsing speed may be very slow.
Tor Browser is not the best choice for streaming and downloading, and its creator strongly opposes torrent downloading. Downloading using Tor is not only slow, but the download traffic is not protected, and it may expose your IP address.
If you are looking for a way to stream or download, VPN will provide you with better protection.
Another disadvantage of using the Tor browser is that it may attract attention to your online activities. Your Internet Service Provider (ISP) cannot see what you are doing, but they know that you are using Tor, and they are suspicious of what you are doing.
Even if you only use the Tor browser to browse the Internet legally, connecting to Tor may make you a target of government surveillance. U.S. government agencies such as the National Security Agency and the FBI are actively trying to track the online activities of Tor users.
Tor with VPN
Tor browser is quite practical, but it cannot provide the security protection provided by VPN. Fortunately, you don’t have to choose between the two. You can combine Tor browser and VPN to combine its functions and get the best privacy.
There are two main ways to combine Tor browser and VPN. We will explain the flow of these two methods and explain the advantages and disadvantages of each method.
Tor over VPN
To use this method, you must first connect to a VPN and then enter the Tor network. This method has some advantages, including ease of use, because you only need to connect to the VPN and open the Tor browser.
In most cases, this configuration can provide you with enough security and privacy to protect your safety.
Some VPNs make this process easier by providing built-in Tor services. For example, NordVPN’s Onion over VPN service allows you to connect to Tor without a Tor browser.
NordVPN routes your traffic through its secure VPN server, and then routes the traffic directly to the Tor network. The NordVPN service can protect all traffic on your device, not just your browser activity.
Another benefit of Tor over VPN is that all your data will be securely encrypted by the VPN before entering the Tor network. Therefore, Tor’s volunteer operation server will not be able to obtain your real IP address.
Since the VPN will hide your online activities, your ISP will also be unable to detect your Tor connection.
Because your VPN provider cannot see your activities in the Tor network, you can gain a layer of privacy. On the other hand, if your VPN provider records your activity logs, Tor over VPN cannot hide your real IP address or the fact that you are using Tor.
Another disadvantage of this method is that it cannot protect you from malicious exit nodes, because your traffic is not encrypted when it reaches the final destination.
VPN over Tor
When using this method, you must first connect to the Tor network and then connect to the VPN. This process is more complicated than Tor over VPN, because in most cases, you must manually configure the VPN to use Tor.
The biggest advantage of VPN over Tor is that it can protect you from attacks from Tor exit nodes. Your traffic will not go directly from the exit node to the final destination, but will be routed from the exit node to a secure VPN server.
This configuration is therefore very suitable for passing sensitive information.
The disadvantage of this method is that although your ISP and government agencies cannot see your online activities, they can find out your Tor connection.
This method can also prevent the VPN provider from recording your real IP address. However, if you choose a VPN with a transparent no-logs policy, you don’t have to worry about this issue.