How to survive correctly and safely in the dark web? The most authoritative tutorial.
The dark web is a very dangerous place. If you do not do a good job of safety protection, it may cause loss of personal information and property. Please be more careful about the following text:
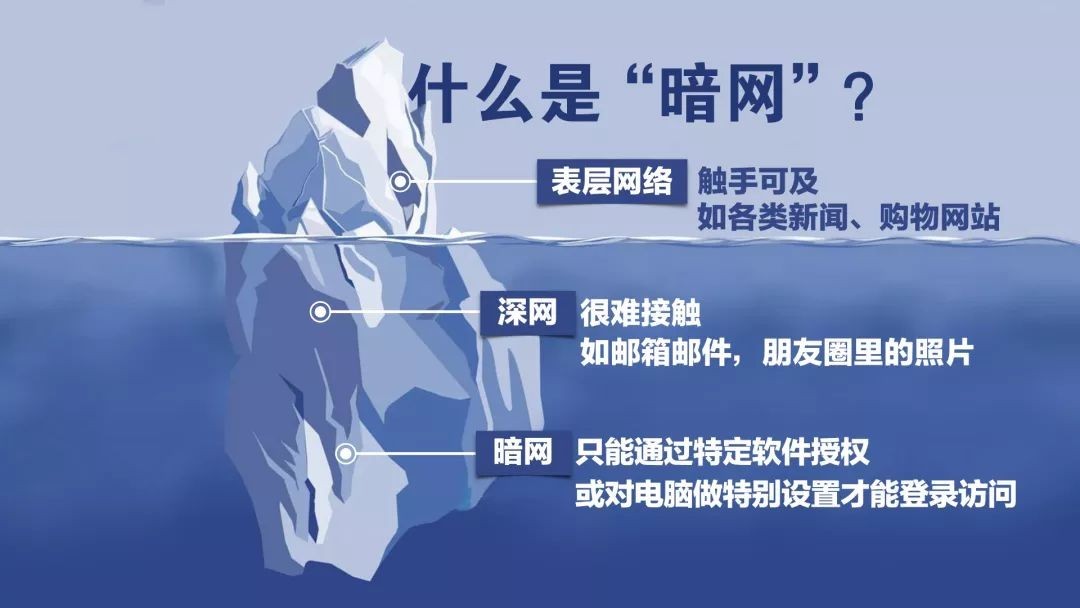
Make sure you master the basics of the dark web
Use mobile real-time operating system (optional)
Use a proxy to encrypt your internet traffic
Download Tor from its official website
Take safety precautions
Forbidden scripts in Tor browser
Change the security level in Tor Browser
Check if there is no IP, DNS or WebRTC leak
Use other anonymous services
Avoid login, subscription and payment
Know where you are going
Use cryptocurrency
Close everything when finished
Realize that you will never be 100% safe
Consult online guides, blogs, search engines, chat sites, etc.
How to do it?
- Make sure you have the basics
This may sound boring. But the dark web is a complicated place, and many things can go wrong. It is full of scammers, malware and phishing websites. Sometimes it is better to learn while doing. However, for the dark web, this is not the best approach. Until you don’t understand how malware works, you’d better not prevent it from infecting malware or losing a lot of money. There are too many people on the dark web who want to abuse their ignorance.
This is why it is important to know exactly what you want to achieve on the dark web before you download software or start browsing. If you know what you want to do or find on the dark web, you can be better prepared:
If you are just looking for something exciting or different: make sure you know how to safely browse the dark web.
If you are trying to monetize Bitcoin or other cryptocurrencies: make sure you understand how cryptocurrencies work, what blockchain is and a reliable platform for dealing with other users.
As a whistleblower, it is important to ensure that you are completely anonymous. Exposing certain things may cost your work, or your freedom in some countries. By remaining anonymous as much as possible, you can prevent cover-ups.
- Use Live Mobile OS (optional)
On the dark web, anonymity is the most important protection. Not because the dark web is illegal (not), but because the more anonymous you are, the safer you are. Unfortunately, operating systems like Windows 10 are not suitable for privacy in the dark web. Windows will perform the following actions that are not conducive to your anonymity:
Your data will be constantly synchronized: browser history, opened websites, application settings and Wi-Fi hotspots will all be tracked
Your device is automatically linked to the unique advertising ID of the third party
Cortana collects data such as: your keystrokes, search results, microphone audio messages, calendar information, music playlists, and even your online purchases
Microsoft can collect all kinds of personal data: your identity, password, habits and interests, user data, contacts and location
If a hacker manages to enter your system through the dark web, all this information may be used by the hacker. Many settings in Windows can be easily turned off (though not all). You can do this through the settings in Windows or using beautiful software such as W10Privacy.
Compared to communicating on the dark web via Windows 10, a better idea is to use a real-time mobile operating system (OS) such as Tails, Whonix, ZuesGuard or Qubes.
- Use a proxy to encrypt your Internet traffic
Even if you use the Tor browser, anyone can track your traffic as long as you have enough time, resources, and expertise. In fact, the Tor browser was found to have vulnerabilities in 2017, which in some cases would leak real IP addresses.
For MacOS and Linux users, the above problems are particularly serious. If these users take precautions and can also run an agent in the background, then their real IP address will not be compromised.
Therefore, it is strongly recommended that you use a proxy in addition to Tor when browsing the dark web.
The proxy encrypts your network traffic and ensures that your IP address will not be monitored by any hacker or government, even if there are loopholes in the Tor browser.
But please note that not every agency provider is equally reliable. The free version often suffers from slow service speeds, data limitations and security vulnerabilities.
- Download Tor from the official website
Mobile real-time operating systems such as Tails and Whonix have the Tor browser pre-installed, so if you use them, you can skip to step 5. For Windows, Mac, Linux or Android users, this is important.
The Tor browser is an interesting target for hackers and government agencies. The fake Tor browser version is designed to destroy users before they even visit the dark web, or to monitor user behavior on the dark web. The latter method is particularly attractive to government agencies.
Therefore, you should always download Tor Browser from its official website: https://www.torproject.org/
Make sure to always download the latest version of the browser and always keep it up to date. In this way, you will ensure that you have the latest security protection measures.
What exactly is Tor?
Tor is a special browser that can be used to access the dark web. Most browsers (such as Chrome and Firefox) can access all regulated websites. All unregulated websites cannot be accessed through these browsers.
Although Tor is known for allowing people to access the dark web, most users just use a browser to access the surface web (the “normal” Internet).
Therefore, always download the correct version of Tor from its official website https://www.torproject.org/.
Make sure to always download the latest version and always approve the update as soon as it becomes available. In this way, you can be sure you have the safest version of Tor.
.onion address
With Tor Browser, as long as you have an address, you can visit any website. Many websites on the dark web have URLs ending in “.onion”. If you use a regular browser to enter such an address, you will not see anything.
Tor ensures that users can browse anonymously. All your requests in the browser are transmitted through the network of other computers, and they are constantly unpacked to reach the destination. Your browsing request will go through a protection node, several relay nodes, and finally an exit node to retrieve the content you requested. In this way, it is impossible for others to track your browsing behavior.
- Take safety precautions
Before opening Tor Browser, you should:
Close all non-essential applications on the computer, such as Netflix, password manager.
Stop running unnecessary services, such as OneDrive.
Install a reputable and fully updated antivirus program on the device.
Install quality and latest anti-malware software. For more general information about malware, see the “Malware” section.
Turn off your location on the device. Your location can be found by the IP address and the device itself.
In Windows 10, you can turn off location from “Settings”> “Privacy”> “Location”> “Turn off location + delete location history”
For macOS: System Preferences>Security and Privacy Panel>Privacy>Uncheck “Enable Location Services”
For Tails or other real-time operating systems: you don’t have to worry about location leaks.
The dark web is full of hackers who will seize any opportunity to take advantage of any details you might have overlooked. If hackers from the dark web manage to break into your system, all the apps and services you run in the background are vulnerable.
Essentially, the best way to stay safe on the dark web is to ensure that potential hackers have little or no information. This means that you should not browse the dark web or spread personal information at will. Don’t click any suspicious links. Leave as few traces as possible. These precautions will reduce your chances of becoming a target.
After opening Tor Browser, do not change the size of the Tor Browser screen. Strangely, this will make you safer. Also, for safety’s sake, please do not type directly in the Tor browser. Instead, type the search in Notepad and copy it to the browser. The advanced method of tracking can identify your specific typing style.
Checking the tracking security of your Tor browser (or for everyday browsers that are not on the dark web) will also not help. Panopticlick allows you to check whether your browser is protected with a single click: ad trackers, invisible trackers, so-called “acceptable ads” and digital fingerprints.
- Forbidden scripts in Tor Browser
Scripts on the website can be used to track your online behavior: they become part of your digital fingerprint. Tor includes a nice feature in its browser to ensure that no website can run scripts on you. To activate this feature, go to the upper right corner of the browser and click on the symbol with the letter “S”. Select the “Enable Restrictions Globally” option and everything is fine.
It’s important to change these settings, because websites often run scripts without notifying you. Since the .onion website is not regulated and is surrounded by malware, this is especially dangerous on the dark web. By blocking scripts, you can reduce the chance of your computer being infected. However, even blocking scripts will not protect you from all harm. Therefore, you should still be mindful when browsing the dark web.
In order to verify whether you have successfully banned the script in the Tor browser, please check the “S” in the upper right corner. If there is an exclamation mark next to it, the website may still be running an unauthorized script. If there is no exclamation mark, you can avoid any unnecessary scripts.
If you want to disable scripts that are used daily in other browsers, it is best to do this through extensions.
Chrome or Brave: script safety
Firefox: NoScript
With these two extensions, you can decide which websites can run JavaScript and which websites cannot run JavaScript. Please note: Both of these extensions can turn off various regular web functions by disabling JavaScript.
- Change the security level in Tor Browser
It can also improve the security level of the Tor browser itself. You can do this by clicking the Tor logo in the upper left corner. Now select “Security Settings”. A window will pop up allowing you to change the security level from it to high.
Naturally, the highest setting is the safest. Unfortunately, this setting will greatly reduce your Internet connection speed and cause some websites to not function properly. The highest security settings will disable most video and audio formats, some fonts and icons may not display correctly, JavaScript is disabled, some images may not display correctly, etc.
Tor includes this security setting, and its exact intention is to protect its users from the threats of many sites on the dark web, which may try to control your device or spread malware. However, this setting is restrictive because it does not allow you to access the dark web without restrictions. In the end, this is a decision between security and access. We recommend sticking to the highest security settings.
- Check for IP, DNS or WebRTC leaks
Even after taking all these safety precautions, you may still face IP or DNS leaks. This means that through some kind of error or leak, your IP address can still be traced back to a third party.
WebRTC has been integrated into most browsers to allow real-time communications such as voice and video calls. This allows you to talk directly in the browser using a webcam, microphone or headset. The problem is that most voice calls are sent over a peer-to-peer connection, which requires your exact IP address. So, for example, if you are using Google Chrome and are running WebRTC, the actual IP address will be displayed even if you are using a VPN.
The above problem is especially common in Google Chrome browser. To subvert this feature, you can install this Chrome extension.
To check if your connection is truly anonymous, please visit the following website:
ipleak.net
dnsleaktest.com
WebRTC test
On these pages, you can check whether your real IP address is visible. All these websites basically do the same thing. At the top of the page, your public IP address is visible, and below it is your location. If your VPN is operating normally, your real address and IP address will not be visible anywhere on the page.
- Use other anonymous services
Even if you enter the dark web completely anonymously, it is still possible to accidentally disclose your personal information by using some online services (such as search engines, extensions, file sharing, messengers, emails, etc.).
Many online services use cookies, trackers and scripts to collect specific data about you. Therefore, it is best to choose an alternative online service that values privacy. You can find many services below that can protect your privacy.
Anonymous search engine
For a good private search engine, you can use the search engine DuckDuckGo instead of Google. Although most search engines cannot run on the dark web, DuckDuckGo can. Alternative search engines that can run on the dark web are SearX and Startpage
Security Code
On the dark web, secure passwords are more important than on the regular (surface) web. If you don’t want the hassle of thinking up a decent password every time and storing them securely, you can use a good password manager. There are two good choices: Bitwarden and LessPass. Both are free and open source. The best option is to load these services through their website.
encrypt documents
If you want to download or upload files on the dark web, it is best to encrypt them. PeaZip is a reliable, free and open source encryption tool. The tool supports 181 different file types. Unfortunately, PeaZip is not available for macOS users. The alternative for Mac users is Keka.
Anonymous upload/share
If you want to share files anonymously, then OnionShare is a good choice. It is available for Windows, macOS and Ubuntu. Dropbox and other similar file sharing software are notorious for not respecting the privacy of users or data. With OnionShare, you can share files of various sizes through a network server.
Another method is Firefox Send. Although it was designed by the creator of Firefox, you can also use it outside of the Firefox browser. With this service, you can share up to 1 GB of files, or, if you create an account, you can share up to 2.5 GB of files per upload-we don’t recommend this.
Anonymous office service
If you are looking for a more secure alternative to Google Docs, check out Etherpad. The software is completely open source, you don’t even need an account to use it. Another option is Cryptpad. You can use it to write text, create spreadsheets or make short presentations. Only the person who has the access key can access the file.
Video call (VoIP)
For (video) calls, you can use many good services, such as Linphone or Mumble. Linphone is a free and open source code that can be used on Windows macOS, IOS, Android and GNU/Linux. The software has end-to-end encryption.
The grumble sound is a little different. It is specially designed for the game and does not keep any logs or record any conversations. But it does not have any end-to-end encryption. The software can be used for Windows, macOS X, IOS and Ubuntu.
Send anonymous message
Compared with standard messaging applications, Ricochet or Signal provides a more secure method of text messaging. Another good option is TorChat. The app is part of Tor and allows you to chat with anyone who also uses it. You do not need to register. TorChat automatically assigns you a digital ID, and you must send that digital ID to other people you want to talk to. You can do this by telling the other party directly (face-to-face) or sending your ID number via encrypted email (see next step). When chatting, you usually won’t be able to get anywhere else, which will allow a high degree of anonymity.
Send emails securely and anonymously
ProtonMail is an acclaimed online email service. Their mail accounts have standard end-to-end encryption. Emails sent via Gmail or Hotmail are usually easy to intercept and/or decrypt. An encrypted email service is a more secure option. These services do tend to have stricter data restrictions. Therefore, if you plan to exclusively use encrypted email accounts, you may want to create multiple accounts.
It is also possible to create a temporary email address (so-called recorder). The advantage of this is that you can create an online account on any website, confirm the registration, and then no longer have to worry about receiving useless emails from that website to bomb your inbox. Some well-known temporary email address providers: TempMail, 10minutemail and Guerrillamail.
If you really don’t want to switch to another email address for dark web browsing, at least make sure that your standard email account gets some extra protection (very good privacy) through PGP. This can be done by adding other services on top of regular email accounts such as Mailvelope. This service can be used with providers such as Gmail or Hotmail. Note that this option is not as secure as temporary email addresses or encrypted email addresses. You can trace back many information about you through your regular email address.
- Avoid logins, plugins, subscriptions and payments
If you want to browse the dark web safely, anonymity is your best choice. If you choose to log in to certain user accounts or bank accounts, your anonymity will be compromised.
Logging into your online bank account on the dark web is never a good idea. After logging in to the user account, every activity on the site can be attributed to the profile, whether it belongs to Tor or not. Therefore, it is best not to log in to any profile or account while browsing the dark web.
However, some websites require you to have an account to access. In this case, you can create a random, disposable email address, create an account that cannot be personally identified, and then use that account to browse the website.
- Creating a user account that cannot be traced back to you means not using your name, birthday, hobbies, interests, location, etc. The better the randomness and anonymity, the better. For more help on how to create a secure password, please refer to this guide.
Most people use at least some plug-ins in their browsers. Many of these plugins can collect personal information about you, your location and your online behavior. Therefore, it is best not to enable these features when searching the dark web.
- Know where you are going
The dark web does not have a regular search index, such as Google. Before entering the dark web, you must know where to go. This means preparing a specific URL to reach the correct page. Random visits to websites are unwise, because it is easy to get to places you don’t want to be. The dark web hosts some of the most unpopular elements on the Internet, such as child pornography sites.
In order to have a certain sense of direction on the dark web, there are some directory sites that can help you find what you need. One of the most frequent places visited by many first-time users is the “hidden Wiki”.
- Use cryptocurrency
The dark web has various markets (the most famous being the now closed Silk Road). Many of these markets may sell illegal products in your country. Therefore, before buying anything on the dark web, you should be careful and pay attention to the laws of your country.
However, not all items sold on the dark web are illegal. Moreover, you may also want to purchase something legally and anonymously. Not all goods you buy are necessarily public knowledge.
All financial transactions on the dark web are conducted through cryptocurrency, rather than through regular bank transfers or credit cards. This is to ensure the anonymity of you and the seller.
Bitcoin is often the name people think of when they hear cryptocurrency. It has a well-known name and is generally considered safe, reliable and anonymous. However, this is not entirely correct.
Bitcoin has many privacy issues, such as address reuse, connected nodes, tracking cookies, and blockchain analysis. This means that someone may link your personal information to the transaction. Thus, the preferred option is to use privacy-conscious coins. The two most popular are Monero and Monero, although there are other options available.
However, before buying something on the darknet, make sure you understand the laws of the country and how cryptocurrencies work.
Close everything when done
After you browse the dark web pages, make sure to close all browser windows and all other related content. If you are using Tails, shut down the operating system and return to the regular operating system. To be safe: please restart quickly.Realize that you will never be 100% safe
Even if you faithfully perform all the previous steps, you still cannot guarantee complete security on the dark web. You can inadvertently provide personal information or click on broken links. Hackers are always looking for new ways around security systems and settings. None of the previous steps will protect you from hardware damage. If your computer hardware is infected with a certain type of malware, any Internet usage is already at risk.
In short, you can take many steps to improve the security of the dark web, but nothing is foolproof.
Check online guides, blogs, search engines, chat sites, etc.
Finding a way out on the dark web can be very difficult. Therefore, we have collected some resources that can be used to further help you. You don’t have to rely only on directories. Please note that these sites may contain cunning characters or even complete malware. Nothing is really safe on the dark web. Don’t trust anyone, use common sense at your own risk.
Darknet Exchange Group
tg: https://ssrshare.github.io?id=1
youtube: https://www.youtube.com/channel/UCsK-77GirO3K9IOoaBQlA0w